Internet still threatened by phishing
NEW YORK – Computer worms raced around the world, leaving behind tools that spread spam. Scammers sent e-mail to trick bank account holders into revealing passwords. Rogue programs known as “spyware” hijacked Web browsers and crippled computers.
These were among the top Internet threats of 2004 as the perpetrators grew smarter and more sophisticated, driven more than ever by economic gains. And while technology to combat such threats has improved, experts concede that’s not enough to address what’s bound to emerge in the coming year.
“The bottom line is, there is no silver bullet technology,” said Gregg Mastoras, senior security analyst at security vendor Sophos Inc. “I just don’t think users are educated enough when they are on machines and what they are doing with it.”
The past year saw more industry attention to security: Microsoft Corp. upgraded its flagship Windows XP operating system, America Online Inc. gave away free security tools, and computer makers began installing software to combat spyware.
Dozens of products and services were developed to attack “phishing” – e-mail pretending to be from trusted names such as Citibank or Paypal, but directing recipients to rogue sites.
But developers of malicious code have gotten better at automating their tools, as well as sharing information about vulnerabilities and techniques to exploit them through underground message boards and chat rooms, said Mark Rasch, chief security counsel for Solutionary Inc.
No longer are bragging rights the primary motive.
“It used to be cool to bring down sites, almost (like) graffiti for the 21st century,” said Arthur Coviello Jr., chief executive for RSA Security Inc. “Today’s worms and viruses are far more detailed, and specific attacks are directed at individuals and businesses for the purpose of economic, ill-gotten gains.”
Virus writers use viruses like “Mydoom” to deposit programs that let them take over infected PCs – and then use them to relay spam or launch attacks on Web sites like Microsoft’s. And once they’ve commandeered such PCs, they form networks of “zombies.” Spammers buy access to these networks so they can send e-mail that appears to come from legitimate home computers, making them harder to tag as junk.
Much of the malicious code appears to originate in countries without adequate laws to prosecute, experts say.
Meanwhile, law enforcement agencies and service providers are only beginning to establish guidelines for jointly chasing suspects who can move about with stealth in a medium that knows no borders.
Security experts rank phishing and spyware as the greatest threats for 2005, given how clever their developers have gotten in the past year.
Unlike spam pitching relatively cheap products like Vioxx, phishing scams can quickly drain entire bank accounts of unsuspecting users.
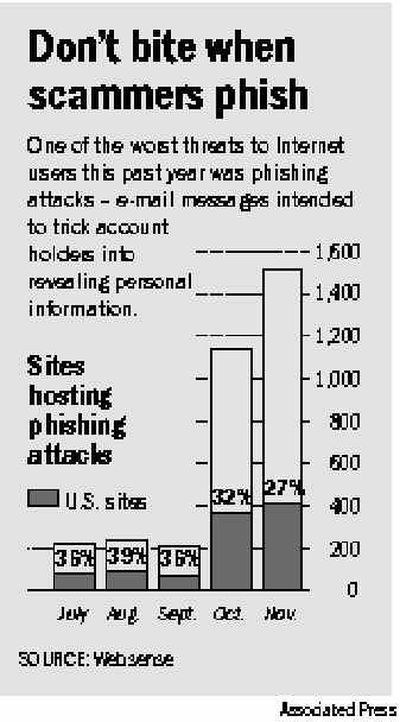
The number of rogue sites used for such scams grew sevenfold in just four months – to 1,518 in November, from 221 in July – according to Websense Inc., which compiles such data for the industry-backed Anti-Phishing Working Group.
Some security experts recommend using a non-Microsoft browser like Mozilla Firefox to reduce spyware and other threats. But in 2005, flaws with those alternatives are likely to emerge as they become more popular and more heavily scrutinized.
Users will need to bear the responsibility for security as much as software developers and service providers, said Johannes Ullrich, chief technology officer with the SANS Internet Storm Center, a research organization.
“Think about traffic,” he said. “You do need good cars. You need good drivers. You need good roads. If any one of those isn’t there, you’ll end up with accidents.”